|
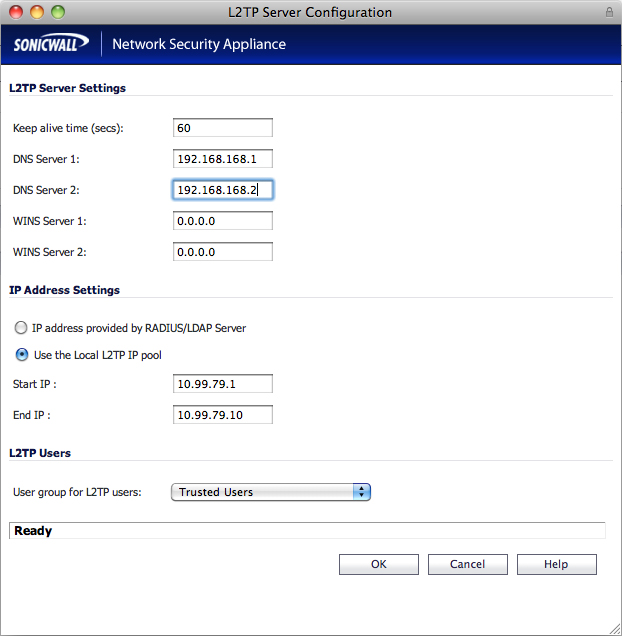
start ip: 10.99.79.1 (this is the start ip of the l2tp network you created earlier) end ip: 10.99.79.10 (this is the end ip of the l2tp network you created earlier) user group for l2tp users: trusted users (or everyone if you prefer)
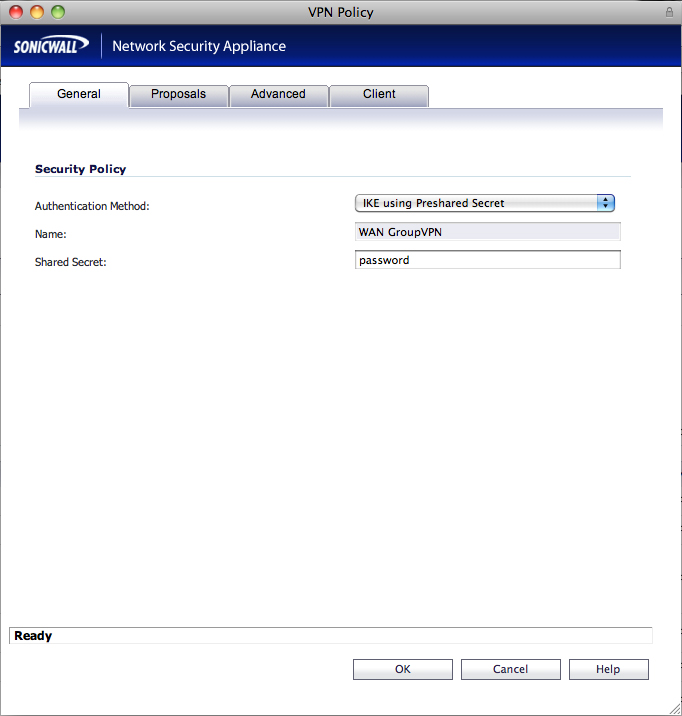
9 - from the sonicwall nsa menu, whilst still in vpn select settings 10 - configure the wan groupvpn policy with the following settings: general tab shared secret: password (well, enter your password here)
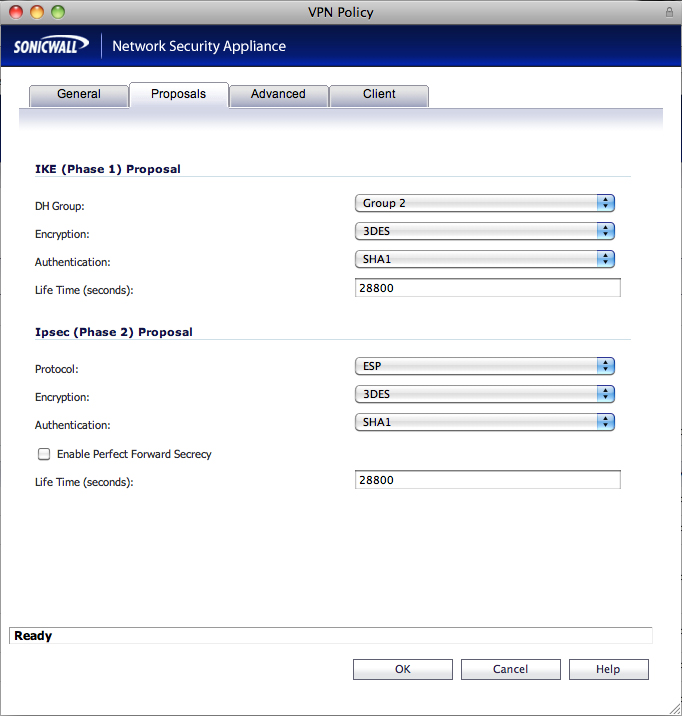
proposals tab ike (phase 1) proposal dh group: group 2 encryption: 3des authentication: sha1 life time (seconds): 28800 ipsec (phase 2) proposal protocol: esp encryption: 3des authentication: sha1 enable perfect forward secrecy: disabled life time (seconds): 28800
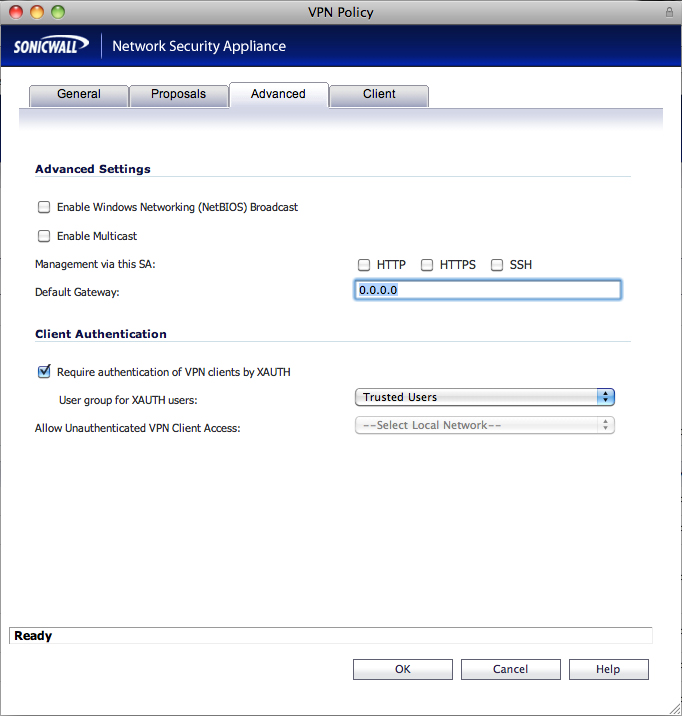
advanced tab enable windows network (netbios) broadcast: enabled enable multicast: disabled management via this sa: unchecked for both http and https default lan gateway: public (wan) ip address of the sonicwall appliance require authentication of vpn clients via xauth: enabled user group for xauth users: trusted users (or everyone) allow unauthenticated vpn client access: disabled
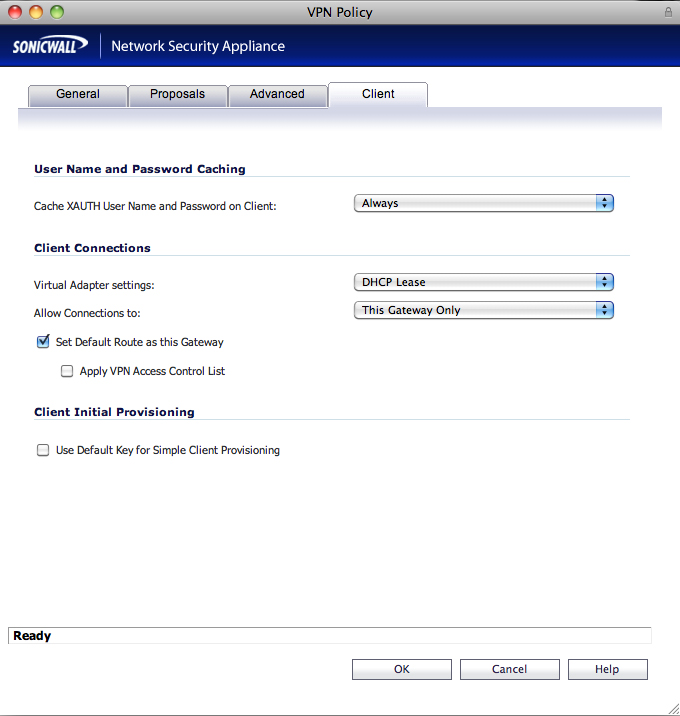
client tab cache xauth user name and password on client: always virtual adapter settings: dhcp lease allow connections to: this gateway only set default route as this gateway: enabled apply vpn access control list: disabled use default key for simple client provisioning: disabled
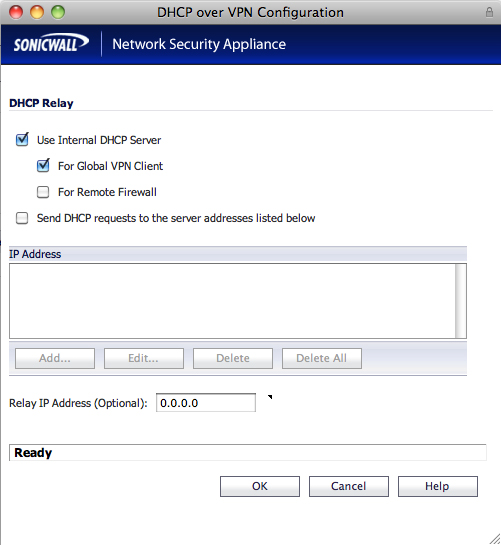
11 - returning to the sonicwall appliance menu, and still in vpn, select dhcp over vpn 12 - select central gateway and click on configure and ensure the following: use internal dhcp server: enabled for global vpn client: enabled for remote firewall: disabled send dhcp requests to the server address listed below: disabled relay ip address (optional): 0.0.0.0
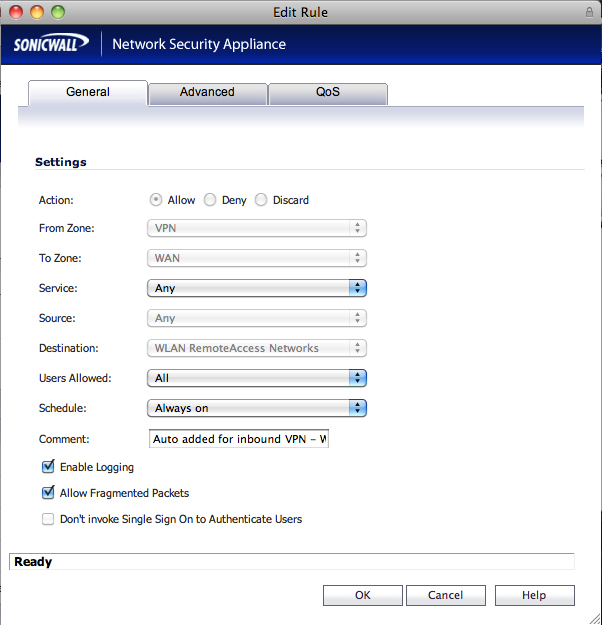
13 - from the sonicwall menu navigate to firewall and access rules 14 - select vpn to wan from the matrix or drop down menu and add the following rule: action: allow from zone: vpn to zone: wan service: any source: wan remoteaccess networks destination: any users allowed: all schedule: always on
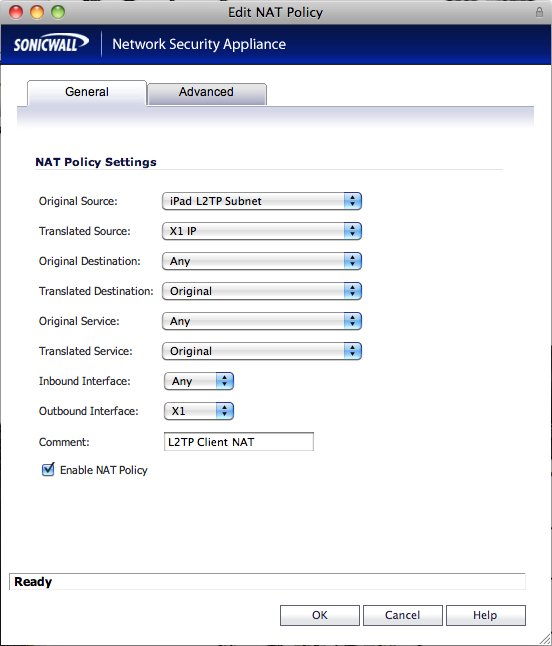
15 - from the sonicwall menu navigate to network and nat policies 16 - add the following nat policy: original source: ipad l2tp subnet (or whatever you created in step 3) translated source: wan primary ip (usually x1 ip) original destination: any translated destination: original original service: any translated service: original inbound interface: any outbound interface: x1 (your wan interface)
17 - from the sonicwall nsa menu navigate to users and local users 18 - create a new user (if one doesn't exist) and then select the vpn access tab and add the following objects: lan subnets wan remoteaccess networks ipad l2tp subnet (or whatever you called the address object that you created in step 3) note: you can add these networks to the trusted users or everyone list if you wish - or individually for users. you must also add any other address objects to which you may require access here. we have used the basic lan subnets for access to the lan above for demonstrative purposes. 19 - click on ok to add the user thats your sonicwall appliance ready! - now go to part 2: setup your ipad / iphone / ipod touch (责任编辑:admin) |