|
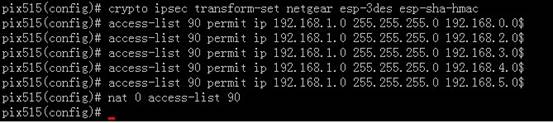
3) 通过vpn传输的数据包不需要做nat,因此,将这些数据包定义到nat 0,nat 0不对数据包进行地址转换,nat0的处理优先始终在其他nat(例如nat1、nat2、nat3……)之前。
对于刚才定义的90号访问列表不做nat转换
pix515e(config)#nat (inside) 0 access-list 90
如下图所示:
3.5.设置加密动态map
由于分支机构的公网ip随时回变动,因此动态的对应加密必须具备在中心的vpn设备上:
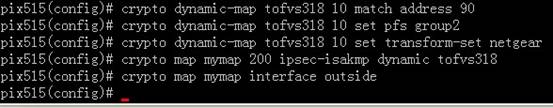
1)定义名称为tofvs318,编号为10的加密动态map并匹配于90号access-list
(注:如果对方vpn公有ip是静态的ip则可使用静态map)
pix515e(config)#
2)对于第10号加密动态map,在ipsec第二阶段使用pfs,dh长度为group 2(1024)
{注:使用pfs(perfect forward secrecy) 来增加安全性,vpn通讯虽然慢点,但是它可以确保为每个ike第二阶段(phase-ii)进行dh交换;该项也为可选,需要和各分支机构对应}
pix515e(config)#
3)第10号加密动态map归到名字为netgear ipsec加密集合
pix515e(config)# crypto dynamic-map tofvs318 10 set transform-set netgear
4) 定义名字为mymap编号为200的静态加密map, 将名字为tofvs318的动态加密map 映射到静态加密map mymap 上.
pix515e(config)#crypto map mymap 200 ipsec-isakmp dynamic tofvs318
5)将静态加密map应用在外部接口上
pix515e(config)#crypto map mymap interface outside
6、打开ipsec的绿色通道并保存配置
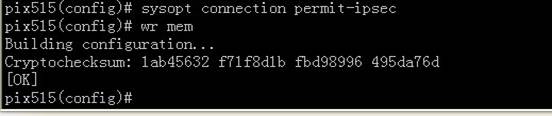
1)指定ipsec的流量是可信任的,即打开ipsec的绿色通道。
pix515e(config)#sysopt connection permit-ipsec
2) 保存配置
pix515e(config)#wr mem
如下图所示:
如果想清除所有配置,可以用命令:’clear config all’ 如下
pix515e(config)#clear config all
7、pix515配置:
pix515# show run
saved:
pix version 6.3(5)
interface ethernet0 auto
interface ethernet1 auto
nameif ethernet0 outside security0
nameif ethernet1 inside security100
enable password 8ry2yjiyt7rrxu24 encrypted
passwd 2kfqnbnidi.2kyou encrypted
hostname pix515
domain-name pix515.com
fixup protocol dns maximum-length 512
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol skinny 2000
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol tftp 69
names
access-list 90 permit ip 192.168.1.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list 90 permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
access-list 90 permit ip 192.168.1.0 255.255.255.0 192.168.3.0 255.255.255.0
access-list 90 permit ip 192.168.1.0 255.255.255.0 192.168.4.0 255.255.255.0
access-list 90 permit ip 192.168.1.0 255.255.255.0 192.168.5.0 255.255.255.0
access-list 90 permit ip 192.168.1.0 255.255.255.0 192.168.6.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
ip address outside 58.62.221.131 255.255.255.248
ip address inside 192.168.1.1 255.255.255.0
ip audit info action alarm
ip audit attack action alarm
no failover
failover timeout 0:00:00
failover poll 15
no failover ip address outside
no failover ip address inside
pdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list 90
nat (inside) 1 192.168.1.0 255.255.255.0 0 0
conduit permit icmp any any
route outside 0.0.0.0 0.0.0.0 58.62.221.129 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h225 1:00:00
timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00
timeout sip-disconnect 0:02:00 sip-invite 0:03:00
timeout uauth 0:05:00 absolute
aaa-server tacacs+ protocol tacacs+
aaa-server tacacs+ max-failed-attempts 3
aaa-server tacacs+ deadtime 10
aaa-server radius protocol radius
aaa-server radius max-failed-attempts 3
aaa-server radius deadtime 10
aaa-server local protocol local
no snmp-server location
no snmp-server contact
snmp-server community public
no snmp-server enable traps
floodguard enable
sysopt connection permit-ipsec
crypto ipsec transform-set netgear esp-3des esp-sha-hmac
crypto dynamic-map tofvs318 10 match address 90
crypto dynamic-map tofvs318 10 set pfs group2
crypto dynamic-map tofvs318 10 set transform-set netgear
crypto map mymap 200 ipsec-isakmp dynamic tofvs318
crypto map mymap interface outside
isakmp enable outside
isakmp key ******** address 0.0.0.0 netmask 0.0.0.0
isakmp policy 9 authentication pre-share
isakmp policy 9 encryption 3des
isakmp policy 9 hash md5
isakmp policy 9 group 1
isakmp policy 9 lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0
terminal width 80
cryptochecksum:9c7fe2af17b050e7ecc7d4a1eb37012d
: end
pix515#
4.分支机构各netgear vpn设备的配置
4.1.fvs114配置
(责任编辑:admin)
(责任编辑:admin) |





